Taking control of your cryptocurrency begins with proper setup and security. Trezor.io/start is the official starting point for using your Trezor hardware wallet, offering step-by-step guidance to safely store, manage, and protect your digital assets. Whether you’re new to crypto or upgrading your security, this guide will walk you through the essentials of Trezor, helping you confidently secure your crypto journey.
Unlike software wallets or exchange accounts, Trezor hardware wallets store your private keys offline, a method known as cold storage. This keeps your assets safe from online threats such as hacks, malware, and phishing attacks.
Trezor wallets are trusted globally for their combination of advanced security, ease of use, and support for thousands of cryptocurrencies, including Bitcoin, Ethereum, and ERC-20 tokens. By pairing a Trezor device with Trezor Suite, you gain full control over your crypto while maintaining the highest security standards.
Trezor.io/start is the official onboarding page that ensures a safe, verified, and step-by-step setup process. From this page, you can:
Tip: Always type the URL manually or bookmark it to avoid phishing websites or fake guides.
Trezor wallets come in models such as Trezor Model T and Trezor One. When first powered on, your device will guide you to either create a new wallet or recover an existing one using a recovery seed.
Important: Never use a device pre-configured with a PIN or recovery seed. Always initialize your wallet yourself.
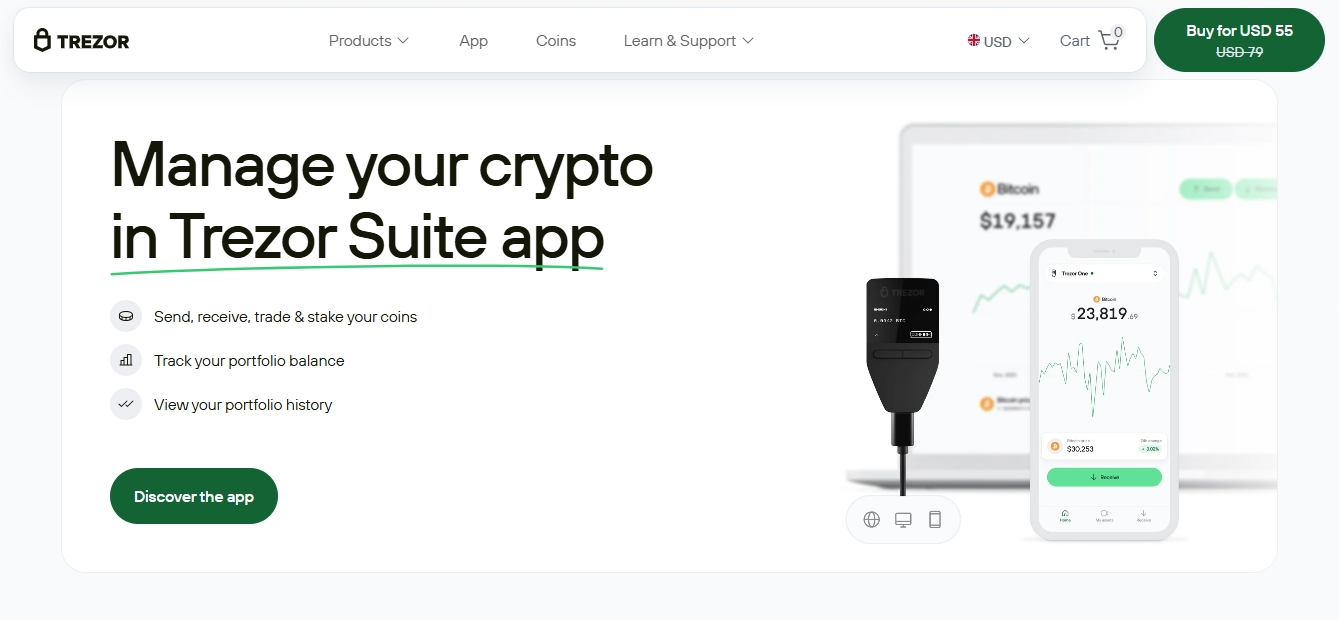
Trezor Suite is the official software for managing your Trezor device. Download it only from trezor.io/start to ensure authenticity.
Trezor Suite allows you to:
Your PIN code protects your Trezor device from unauthorized physical access. Choose a unique PIN that is not easy to guess. After multiple incorrect attempts, the device will reset to protect your assets.
Trezor generates a recovery seed — a list of 12, 18, or 24 words — which acts as a master key to your wallet. This seed is essential for recovering your crypto if your device is lost, stolen, or damaged.
Best Practices:
Trezor staff will never ask for your recovery seed.
Trezor Suite includes a verification process to confirm that your hardware wallet is genuine and untampered. This ensures your device meets Trezor’s strict security standards before storing any funds.
After setup, Trezor Suite becomes your central hub for managing cryptocurrency safely.
Trezor Suite provides a clear overview of all your accounts, including balances, transaction history, and total portfolio value. You can track multiple wallets across different blockchains in one interface.
Transactions are signed on your Trezor device, ensuring private keys never leave the hardware wallet. When receiving crypto, Trezor Suite generates a secure address verified on your device before use.
Trezor Suite integrates with trusted partners to let you buy, sell, or swap supported cryptocurrencies directly in the application. This reduces reliance on external exchanges while keeping your private keys secure.
You can stake supported cryptocurrencies like Tezos, Polkadot, and Algorand through Trezor Suite. Rewards are credited directly to your device, ensuring safety and full control.
Trezor Suite manages firmware updates for your device and allows installation of blockchain apps. Updates are crucial for security, support for new coins, and feature improvements.
Trezor wallets, combined with Trezor Suite, offer multiple layers of protection:
Even if your computer is compromised, Trezor Suite ensures that your crypto remains safe.
Many crypto losses occur due to simple mistakes. Avoid these when using Trezor:
Following best practices keeps your crypto safe from both online and physical threats.
Trezor hardware wallets are ideal for:
If you believe in the principle “not your keys, not your coins,” Trezor is the perfect solution.
Trezor.io/start provides access to official tutorials, setup guides, and troubleshooting resources. Verified guides help you securely set up your device, recover wallets, and manage assets without exposing your private keys.
Avoid advice from unofficial forums, as incorrect guidance can put your crypto at risk.
Security doesn’t stop after setup. To protect your cryptocurrency over time:
Consistent vigilance ensures your digital assets remain fully under your control.
Trezor.io/start is your gateway to safe and confident cryptocurrency ownership. By following the official setup instructions, securing your recovery seed, and using Trezor Suite responsibly, you ensure your assets remain protected from threats.
Trezor hardware wallets, combined with Trezor Suite, give you peace of mind, advanced security, and an intuitive platform for managing crypto. Begin your journey today, take full control of your digital assets, and experience secure self-custody with Trezor.